Security audit process of a WordPress instance
(Oh my,) what have I done
- CERT.LV's Security experts group, Founding member
- IT security company 1st Ltd, Founder
- Latvian MoD, National Cyber Security Policy Coordination Section, Senior Expert
- National Expert of Latvia on the NIS Directive
Procedures for ensuring information and communication technology system compliance to the minimal security requirements
Regulation No 442 of the Cabinet of Ministers (Latvia)
- Minimal technical security requirements for all (two categories)
- Requirement to create security policy document(s)
- Penetration tests
- Outsourcing requirements
possible.lv
- Data acquisition and analysis
- IT security
- investigation of security incidents
- security consulting
- penetration testing
- IT security audit
Get on with it!

WordPress used by diverse set of actors across all sectors
IT security consists of
Confidentiality
Confidentiality is the property, that information is not made available or disclosed to unauthorized individuals, entities, or processes.
Integrity
Integrity means that data cannot be modified in an unauthorized or undetected manner.
Availability
Availability is the property of the information system to be available when it is needed.
Measured against the defined availability times.
Defense in depth
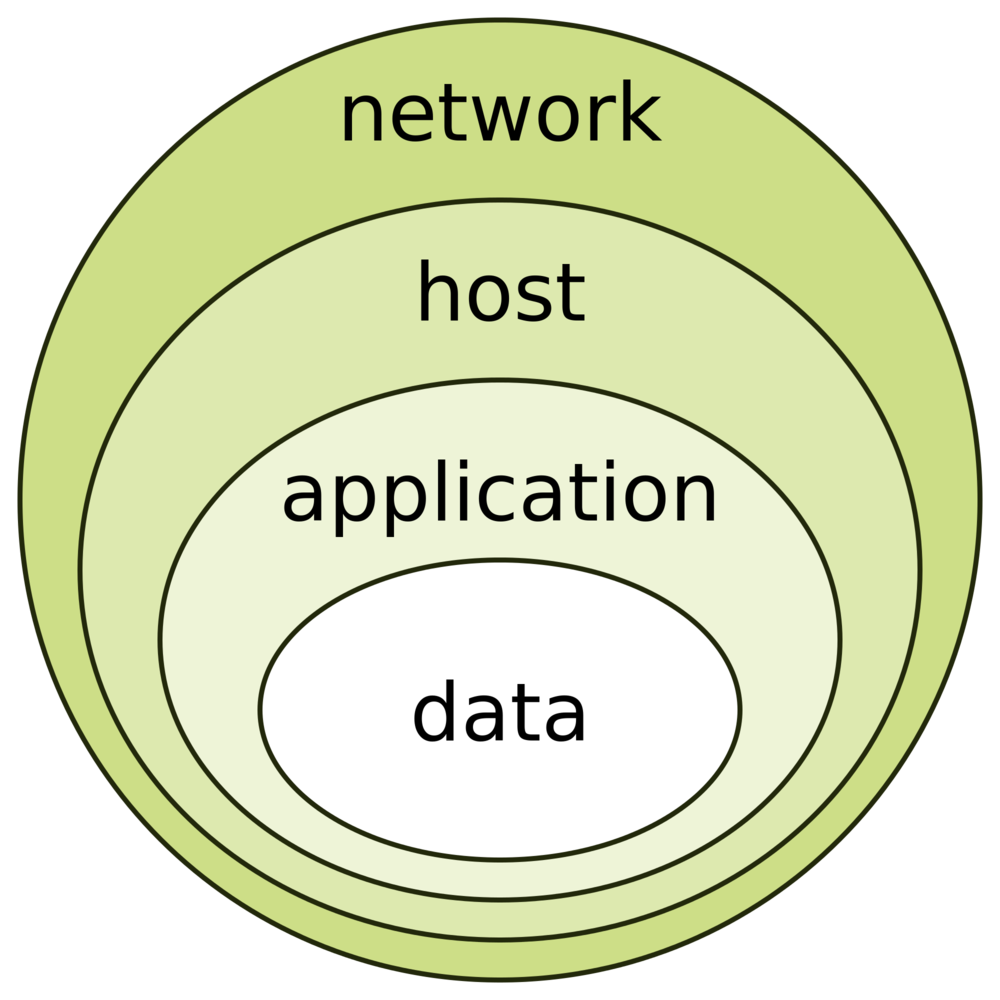
- The defense-in-depth onion model provides defense throughout the lifespan of information from the initial creation to disposal.
- Its goal is to provide redundancy in case a security control fails or a vulnerability is exploited.
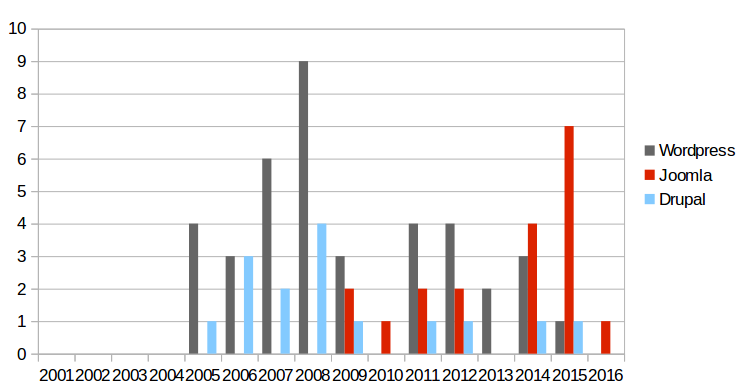
CMS comparison



Adoption (public IPv4)
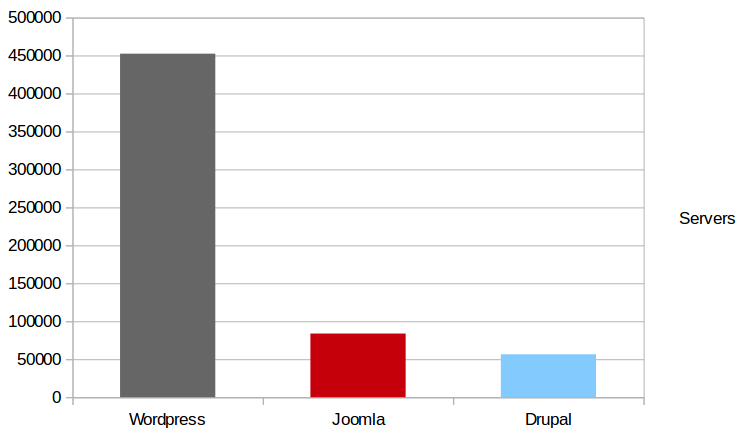












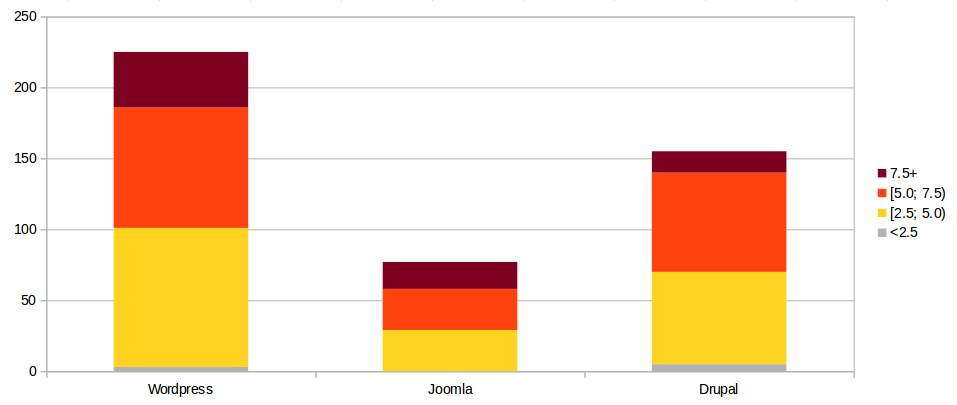
Security comparison
CVSS = Common Vulnerability Scoring System
Each vulnerability scored: 0 (huh? meh!) to 10 (SHTF)
Total vulnerabilities in core by CVSS
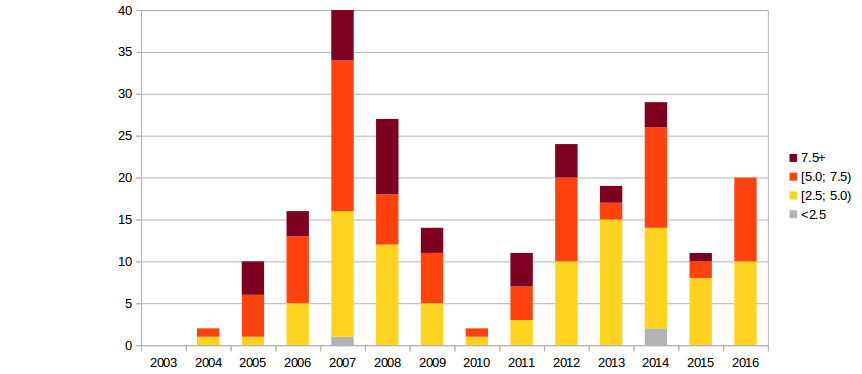
Vulnerabilities in WordPress core by CVSS/year

Vulnerabilities in Joomla core by CVSS/year
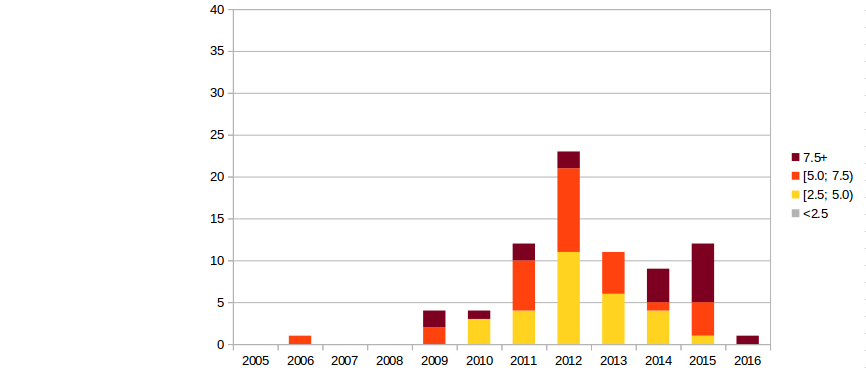

Vulnerabilities in Drupal core by CVSS/year
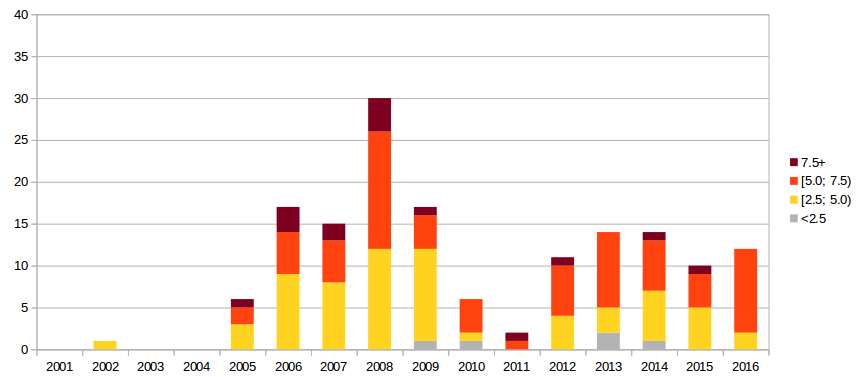

Vulnerabilities with CVSS 7.5 and higher
OK, so what about home-brewed CMS?
+ no publicly known vulnerabilities
- no publicly known vulnerabilities
- requires lots of resources to implement correctly
Remember "MacOS has no viruses"?
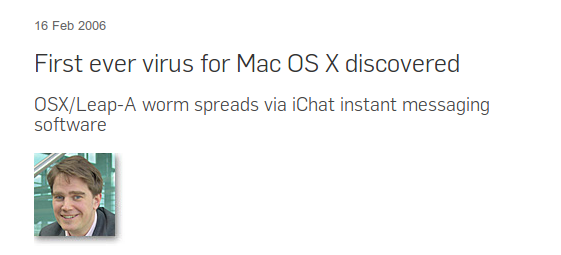
"OH MY GAWD WE'RE ALL GONNA DIE DOWN HERE!!11"
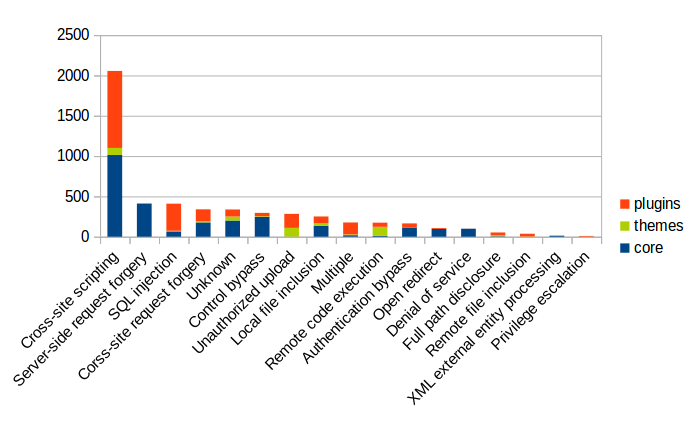
WordPress has security vulnerabilities. What kind of?
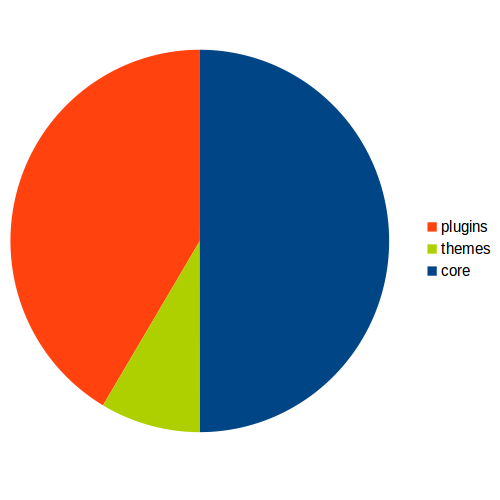
9%
of all themes have had vulnerabilities
| Theme | # of vulns |
|---|---|
| echelon | 5 |
| elegance | 5 |
| fusion | 5 |
| persuasion | 5 |
| awake | 4 |
| construct | 4 |
| dailyedition | 4 |
| method | 4 |
| modular | 4 |
| myriad | 4 |
3%
of all plugins have had vulnerabilities
| Plugin | # of vulns |
|---|---|
| wp-symposium | 14 |
| nextgen-gallery | 12 |
| count-per-day | 11 |
| wordfence | 11 |
| better-wp-security | 10 |
| flash-album-gallery | 10 |
| ninja-forms | 10 |
| usc-e-shop | 10 |
| w3-total-cache | 10 |
| woocommerce | 10 |
| wp-photo-album-plus | 10 |
| wp-super-cache | 10 |
Surely, the core has less vulnerabilities, right?
Sorry
Audit process from A to Z
- Defining scope and threat modelling
- Liability waiver, NDA and contract
- Network level tests
- Machine level tests
- Service level tests
- Application level tests
- Drafting a report
- Client debriefing
Tests are usually carried out according to OWASP ASVS.
V1. Architecture, design and threat modelling V2. Authentication V3. Session management V4. Access control V5. Malicious input handling V7. Cryptography at rest V8. Error handling and logging V9. Data protection V10. Communications V11. HTTP security configuration V13. Malicious controls V15. Business logic V16. File and resourcesV17. MobileV18. Web servicesV19. Configuration
WPScan DEMO
(if time permits)
- Plugin and theme detection,
- user enumeration,
- password bruteforcing
Scared? Don't be!

Just follow these tips and make sure to study the linked material.
Tips (excerpt)
- Harden your LAMP
- Use encryption: SSH, SFTP, VPN, TLS
- Have an offsite up to date back-up
- Remove unused themes, plugins
- Enable auto-updates at risk of breaking stuff
define( 'WP_AUTO_UPDATE_CORE', true );
add_filter( 'auto_update_plugin', '__return_true' );
add_filter( 'auto_update_theme', '__return_true' ); Tips (excerpt)
- Limit access to wp-admin
- Verify file permissions
- Delete readme.html and install.php
- Move wp-config.php one directory level up
- Set your encryption keys
define('AUTH_KEY', 'put your unique phrase here');
define('SECURE_AUTH_KEY', 'put your unique phrase here');
define('LOGGED_IN_KEY', 'put your unique phrase here');
define('NONCE_KEY', 'put your unique phrase here'); Tips (excerpt)
- Consider installing WP Security Audit Log and Security Ninja
- If your page is relatively static, do not expose WordPress to the world; you can use e.g. httrack to download the generated html to your public site
- Ask for help, if you are having difficulties with any of these.
- Finally, request a professional peneteration test.